As of August 30, 2017, our LinkedIn page was hacked. Luckily, after 24 hours, we got it back. As you can imagine, most of us here in Houston, TX, were not too happy. On top of this, there’s the obvious disaster at hand: Hurricane Harvey.
Considering the tremendous losses others have incurred from belongings to homes and even lives, losing access for 24 hours to a social media platform seems like a walk in the park. But it got me thinking….whether you’re an individual sales rep or an enterprise level med-tech company, you need ways to protect yourself, your data, and your intellectual property. Specifically, with LinkedIn, there isn’t much recourse for users to take if a data breach such as this occurs.
Start With LinkedIn Customer Service Recommendations
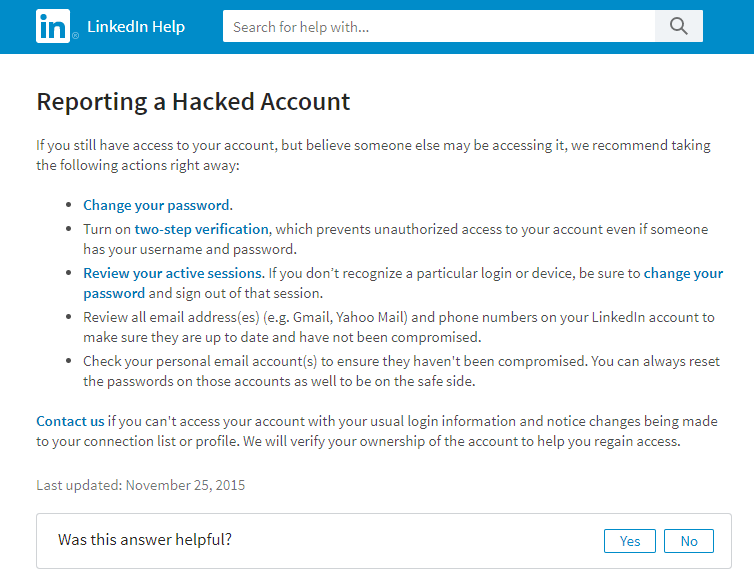
Though this seems obvious, it’s a necessary step — especially reviewing your currently active sessions. If you see anything unfamiliar or suspicious, investigate it right away! The follow up check of your personal and work emails is also a must. You can avoid further compromises in one simple check.
TIP: I run a company and as CEO I can be a bit impatient – like I want results now – so when I have to fill out a bunch of online forms and wait…and wait…well – that doesn’t quite sit well with me. So after much digging I found this email: linkedin_support@cs.linkedin.com – and they responded rather quickly. You just have to be proactive! Also make sure that you have back up emails loaded on your account in case someone does try to change your primary email – they will notify your secondary email that there was a change.
But WHY Did I get Hacked In the First Place?
Great question! No idea. Apparently, hackers like to target LinkedIn accounts for the greater access to network information. Think about it: you can get to know A LOT about a person by looking at their LinkedIn profile. You can even identify more targets by looking at people’s connections. Gaining access to login credentials enables hackers to potentially crack greater codes than just a few LinkedIn profiles.
They target people in many ways, but an old favorite is the classically threatening security themed farce. You can see in the image below that this is a fairly well reasoned email, but it doesn’t look as official as one from LinkedIn should look. It is a phishing email aimed to capture all your details.
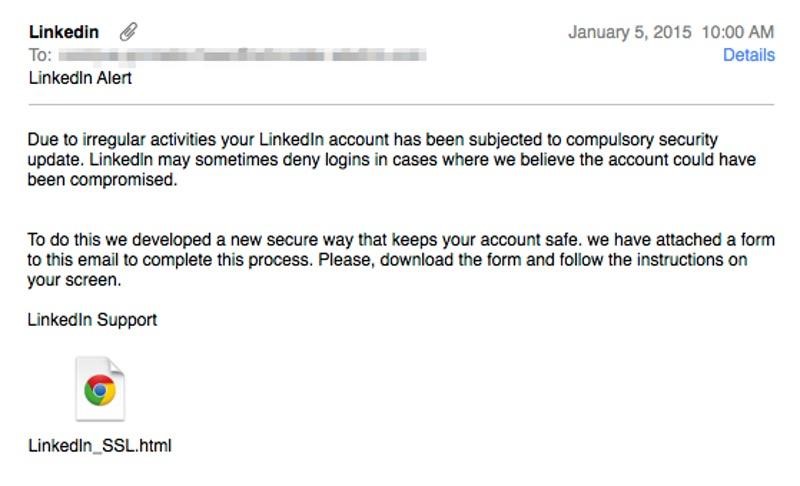
By falling for this email scam and filling out the attached HTML file, you unwittingly hand the hackers your login information on a silver platter. While you might not fall for this, a coworker might. Your parents or your kids might. Who knows? Two-factor authentication is a great way to thwart these kinds of schemes if you have been compromised.
Simple Steps to Security
As we’ve mentioned, getting hacked is no picnic. But there are ways to mitigate the effects of being hacked. The following list is a great way to start:
- Anti-virus software like Avast, Malware Bytes, and Webroot
- Changing passwords every 3 – 6 months
- Encryption or scrambling software
- Proxies or VPNs
- Keeping up with data breaches by following Twitter accounts such as haveibeenpwned as operated by Troy Hunt
- Request a data archive of your profile
- Add a second backup email to your profile
- Download all of your contacts in case you lose your account
Why Do Some People Not Know That They’ve Been Hacked?
Though LinkedIn is great for many things like networking and thought leadership, the communication about security breaches leaves something to be desired. Though there was a ton of coverage on the 2012 LinkedIn data breach that affected nearly 6.5 million users, other breaches were swept under the rug. The reason why: its data from the initial 2012 breach either being released or used years later. That explains why the 2012 data breach gets listed among the worst data breaches of all time regularly.
 What Else Can I Do to Protect Myself?
What Else Can I Do to Protect Myself?
TIP: Go to a website called haveibeenpwned.com. I know — it looks like a spam website, but it’s actually one of your greatest tools in protecting your login information and email security. It automatically checks any email you put in for security breaches or compromises. The person who operates it, Troy Hunt, is a known specialist in this area and regularly writes about data breaches.
Avoid our mistakes: get a data archive, download your connections, and enable that two-factor authentication. Data matters more and more every day. The ProSellus Growth Engineers still have a little growing to do in some departments, but then again, shouldn’t you always be growing?
We’ll let you think on it a bit.

